Virtualisation with KVM
Introduction
of KVM
The
ability to run multiple virtual machines (VMs) on single server
hardware platforms provides cost, system management, and flexibility
advantages in IT infrastructure today. Hosting multiple VMs on single
hardware platforms reduces hardware expenses and helps minimize
infrastructure costs such as power consumption and cooling.
KVM
(Kernel-based Virtual Machine) is the leading open source
complete virtualization solution on x86 hardware and it supports all
major operating systems including Linux and Windows. KVM enables
organizations to be agile by providing robust flexibility and
scalability that fit their specific business demands. KVM converts
the Linux kernel into a bare metal hypervisor and it leverages the
advanced features of Intel VT-X and AMD-V x86 hardware, thus
delivering unsurpassed performance levels.
The
integration of key virtualization technology at the processor level
by both Intel (Intel® VT) and AMD (AMD-V) has enabled virtualization
to be deeply integrated at the Linux kernel level, yielding
significant benefits in terms of performance, scalability, and
security.
Kernel-based
Virtual Machine (KVM) is a cross-platform, open source hypervisor
that provides enterprise-class performance, scalability and security
to run Linux and Windows workloads on x86, POWER and additional
processor architectures. KVM provides organizations a cost-effective
alternative to other hypervisors, and enables a lower-cost, more
scalable, and open Cloud. KVM is ready for business: because it's
open it is cost-effective, because IBM recommends it's a smart
choice.
KVM ADVANTAGES
Hardened
security Organizations can use KVM to create secure, open
virtualization IT environments as well as both public and private
clouds. KVM meets government security standards through Common
Criteria Certification at Evaluation Assurance Level 4+ (EAL4+). It
also provides advanced
security protection between virtual machines through the Mandatory
Access Control security in SELinux.
Enerprise
class performance/Scalability Allows higher densities of
virtual machines per physical server. KVM demonstrated the highest
performance and the highest number of virtual machines running on a
single host. 2 In addition, IBM and Red Hat recently published the
first virtualized TPC Benchmark C (TPC-C) online transaction
processing benchmark, delivering as much as 88 percent of
“bare-metal” performance for demanding business-critical
workloads.
Lower
total cost of ownership (TCO) Because it is open source,
there are no up-front license costs, so KVM can save on software
costs in addition to savings through consolidating workloads. In
fact, KVM has been shown to be 59 percent less expensive over a
three-year TCO, compared
to
competitors.
KVM
represents a truly open solution that delivers real value in terms of
functionality. Organizations save on licensing costs while enjoying
the technical and financial advantages of an open multi-vendor
ecosystem.
Flexibility Enables
support for different management interfaces.
No
vendor lock-in KVM is developed by an open-source
community, helping users avoid being locked in with specific vendors
to proprietary virtualization technologies.
General KVM information
What is the difference between KVM and VMware?
VMware is a proprietary product. KVM is Free Software released under the GPL.Is dynamic memory management for guests supported?
A. KVM only allocates memory as the guest tries to use it. Once it's allocated, KVM keeps it. Some guests (namely Microsoft guests) zero all memory at boot time. So they will use all memory.B. Certain guests (only Linux at the moment) have a balloon driver, so the host can have the guest allocate a certain amount of memory which the guest won't be able to use anymore and it can then be freed on the host.
What OSs can run inside KVM VM?
| Vendor | OS |
| Microsoft | Servers
:Server 2012, Server 2008, Server 2003, Server 2000 Desktops :Windows 10 , Windows 8, Windows 7, XP |
| Linux | All flavours including Fedora, Cent OS, Red Hat, Scientific Linux, Debian, Ubuntu, Knoppix, Suse Linux, Slackware, Gentoo, Arch, |
| Other | BSD, Solaris, Qnx, Dos 6.22, Freedos, FreeDOS 7 + Novell Netware 4.1 , Darvin |
What OSs will * * * not * * * run inside KVM VM ?
| Microsoft | Windows 95, 98, NT, |
| Apple | Os X |
Is the name 'KVM' trademarked?
No.For this it is advised to use Ubuntu 14.04 (LTS ) server edition though other Linux distributions also supports kvm.
Things you need.
1. System capable of running kvm ( refer - pre-requisites ). Maximum ram is advised. HDD can be 200 GB onwards.
2. Ubuntu 64bit Server edition.
3. Internet Connection
4. Switch.
5. Either thin client / laptop / desktop with any os ( Windows / Linux etc )
[ A ] Pre-requisites.
System on which you want to install kvm has to be true 64 bit processor. Intel Xeon proessor could be a right choice.
How to find out whether your system is capable of running KVM is to boot the system with Ubuntu 64bit 14.04 USB stick.
Open the terminal windows with Contol+T key and enter following command.
egrep -c '(vmx|svm)' /proc/cpuinfo
If 0 it means that your CPU doesn't support hardware virtualization.
Use a 64 bit kernel (if possible)
Running a 64 bit kernel on the host operating system is recommended but not required.
- To serve more than 2GB of RAM for your VMs, you must use a 64-bit kernel (see 32bit_and_64bit). On a 32-bit kernel install, you'll be limited to 2GB RAM at maximum for a given VM.
- Also, a 64-bit system can host both 32-bit and 64-bit guests. A 32-bit system can only host 32-bit guests.
To see if your processor is 64-bit, you can run this command:
egrep -c ' lm ' /proc/cpuinfo
If 0 is printed, it means that your CPU is not 64-bit.
If 1 or higher, it is. Note: lm stands for Long Mode which equates to a 64-bit CPU.
Now see if your running kernel is 64-bit, just issue the following command:
uname -m
x86_64 indicates a running 64-bit kernel. If you use see i386, i486, i586 or i686, you're running a 32-bit kernel.
Note: x86_64 is synonymous with amd64. [ B ] Installation :
Step 1. Install Ubuntu 64-bit Server as usual. Do not configure network while installing it.
Now manually configure the network to reflect following/.
[ file is /etc/network/interfaces ] -- use sudo nano /etc/network/interfaces to edit and Cntl+x to save it . Change the network address as per your own settings.
auto eth0
iface eth0 inet manual
iface br0 inet static
address 192.168.1.75
network 192.168.1.0
netmask 255.255.255.0
broadcast 192.168.1.255
gateway 192.168.1.1
dns-nameservers 192.168.1.1
bridge_ports eth0
bridge_stp off
auto br0
Also edit /etc/resolv.conf and add following lines and save.
nameserver 8.8.8.8
nameserver 8.8.4.4
Reboot the system and check whether you are able to ping google.com and ping 8.8.8.8 - to make sure that your system is capable of reaching internet.
Step 2.
Update your newly installed Ubuntu server.
sudo apt-get update
sudo apt-get upgrade
Step 3.
Install kvm packages.
sudo apt-get install qemu-kvm libvirt-bin virtinst bridge-utils sasl2-bin
Once the installation is complete, add user the group libvirtd.
sudo adduser `id -un` libvirtd
[ C ] Settings.
1. Add the option
-l in the file /etc/default/libvirt-binIt should look like.
libvirtd_opts="-d -l"
2. The file
/etc/libvirt/libvirtd.conf uncomment the line ( Remove # )listen_tls = 0 listen_tcp = 1tcp_port = "16509"
3. With your user create a saslpassword
sudo saslpasswd2 -a libvirt username // give your actual username.
Password: xxxxxx
Again (for verification): xxxxxx
4. Allow Firewall to accept connection on port 16509.
Create a file
/etc/ufw/applications.d/libvirtd and it add the following lines[Libvirt]
title=Virtualization library
description=Open port for WebVirtMgr
ports=16509/tcp
Add a firewall rule in the chain
sudo ufw allow from any to any app Libvirt
5. Test it.
virsh -c qemu+tcp://IP_address/system nodeinfo
Please enter your authentication name: username
Please enter your password: xxxxxx
CPU model: x86_64
CPU(s): 2
CPU frequency: 3611 MHz
CPU socket(s): 1
Core(s) per socket: 2
Thread(s) per core: 1
NUMA cell(s): 1
Memory size: 3019260 kB
[ D ] Install Administration Package.
Give following Commands in terminal.
sudo apt-get install git python-pip python-libvirt python-libxml2 novnc supervisor nginx Install python requirements and setup Django environment
git clone git://github.com/retspen/webvirtmgr.git
cd webvirtmgr
sudo pip install -r requirements.txt
./manage.py syncdb
./manage.py collectstatic./manage.py createsuperuser You just installed Django's auth system, which means you don't have any superusers defined.
Would you like to create one now? (yes/no): yes (Put: yes)
Username (Leave blank to use 'admin'): admin (Put: your username or login)
E-mail address: username@domain.local (Put: your email)
Password: xxxxxx (Put: your password)
Password (again): xxxxxx (Put: confirm password)
Superuser created successfully. If you need additional Users . ./manage.py createsuperuser cd .. sudo mv webvirtmgr /var/www/ Add file webvirtmgr.conf in /etc/nginx/conf.d: server {
listen 80 default_server;
server_name $hostname;
#access_log /var/log/nginx/webvirtmgr_access_log;
location /static/ {
root /var/www/webvirtmgr/webvirtmgr; # or /srv instead of /var
expires max;
}
location / {
proxy_pass http://127.0.0.1:8000;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-for $proxy_add_x_forwarded_for;
proxy_set_header Host $host:$server_port;
proxy_set_header X-Forwarded-Proto $remote_addr;
proxy_connect_timeout 600;
proxy_read_timeout 600;
proxy_send_timeout 600;
}
} Save it !! & restart nginx. sudo service nginx restart
Setup Supervisor
sudo service novnc stop
sudo update-rc.d -f novnc remove
sudo rm /etc/init.d/novnc
sudo chown -R www-data:www-data /var/www/webvirtmgr
Add file
webvirtmgr.conf in /etc/supervisor/conf.d: [program:webvirtmgr]
command=/usr/bin/python /var/www/webvirtmgr/manage.py run_gunicorn -c /var/www/webvirtmgr/conf/gunicorn.conf.py
directory=/var/www/webvirtmgr
autostart=true
autorestart=true
stdout_logfile=/var/log/supervisor/webvirtmgr.log
redirect_stderr=true
user=www-data
[program:webvirtmgri-novnc]
command=/usr/bin/python /var/www/webvirtmgr/console/webvirtmgr-novnc
directory=/var/www/webvirtmgr
autostart=true
autorestart=true
stdout_logfile=/var/log/supervisor/webvirtmgr-nonvc.log
redirect_stderr=true
user=www-data
Restart supervisor daemon
sudo service supervisor stop
sudo service supervisor start
Edit /etc/libvirt/qemu.conf
Change following. ( Remove # )
vnc_listen = "0.0.0.0"
vnc_password = "admin123"
Now give following command in terminal
cd /var/www/webvirtmgr
./manage.py runserver xx.xx.xxx:8000
Now from your desktop/ laptop open a browser and do rest things.
for console operation refer the [C}Setting usrname and password. ( You need to test. }
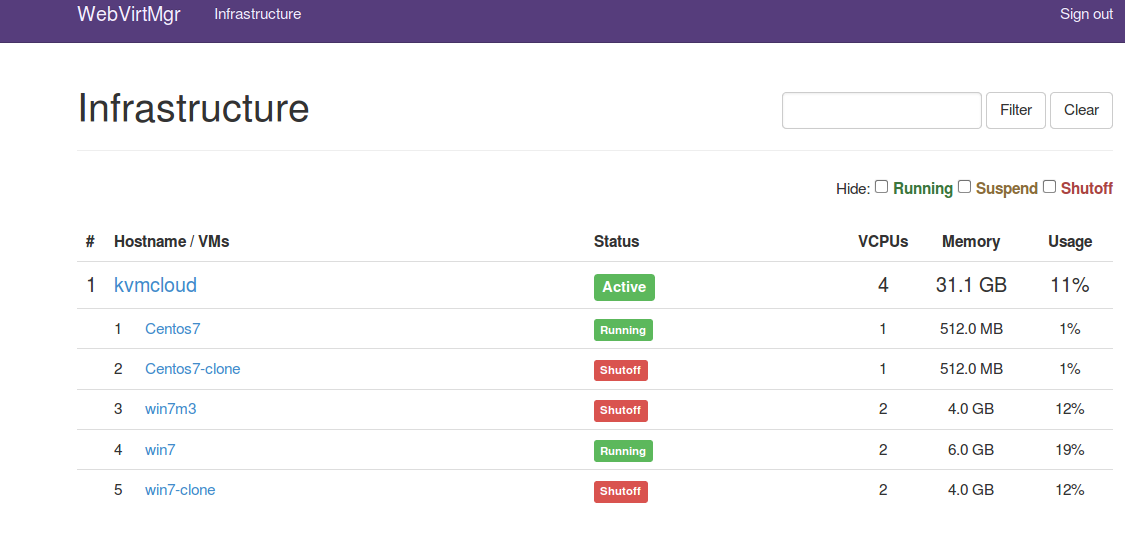
Screen Shots both running Windows 7 and Cent OS Instances.
Good practices for KVM.
1. Use
KVM para-virtualized drivers for disk, memory and network: this is
the starting point for every other optimization.
2.
Use if possible block devices for VM storage: A guest operating
system using block devices achieves lower-latency and higher
throughput;
3.
Asynchronous I/O model for KVM guests: using AIO ( aio=native )
support can improve guest I/O performance, especially when there are
multiple threads performing I/O operations at the same time;
4.
Disk caching: use the writeback option where both the host page cache
and the disk write cache are enabled for the guest.
Once Windows 7 is installed (feel free to run all the Windows updates
and reboots needed), power off the VM, and do the following changes to
your VM Details:
- Sound driver to: ich6 # you may need to use the guest Device Manager and remove the Audio device, and let Windows re-detect it after a reboot.
- Video driver to: qxl # this will require spice-guest-tools-0.1.exe to be installed on the guest, but will allow you more flexibility with your guest screen resolution.
- Display type to: Spice # much faster rendering than VNC, and allows sound to work.
- Processor -> Configuration -> Model: core2duo # By doing this, Windows 7 will stop crashing when you try to shut it down.
- Once all of the above are changed, start the VM again, and download and install the spice-guest-tools
Automated installation of Windows 7 guest Refer detailed instructions on http://linux.xvx.cz/2013/11/automated-installation-of-windows-7-in.html Snapshots :http://sandilands.info/sgordon/automatic-backup-of-running-kvm-virtual-machines HowTo – Integrate Windows Apps into the Ubuntu Linux Desktop using Windows RemoteApp | Education and the Cloud



No comments:
Post a Comment